We have a commitment to ensuring that our journalism is not locked behind a paywall. But the only way we can sustain this is through the voluntary support of our community of readers. If you are a free subscriber and you support our work, please consider upgrading to a paid subscription or gifting one to a friend or family member. You can also make a tax-deductible donation to support our work. If you do not have the means to support our work financially, you can do your part by sharing our work on social media and by forwarding this email to your network of contacts.

During Wednesday’s meeting for Trump’s cabinet, Mike Waltz checked the app on his phone, using what appeared to be Signal. As news broke that Waltz had lost his job as National Security Advisor, images from the cabinet meeting circulated widely online on Thursday. Upon closer inspection of the photos, it turned out that Waltz was not using the traditional Signal app. He appeared to be using an archiving app made by Israeli firm TeleMessage, which sells companion apps meant to enable archiving messages.
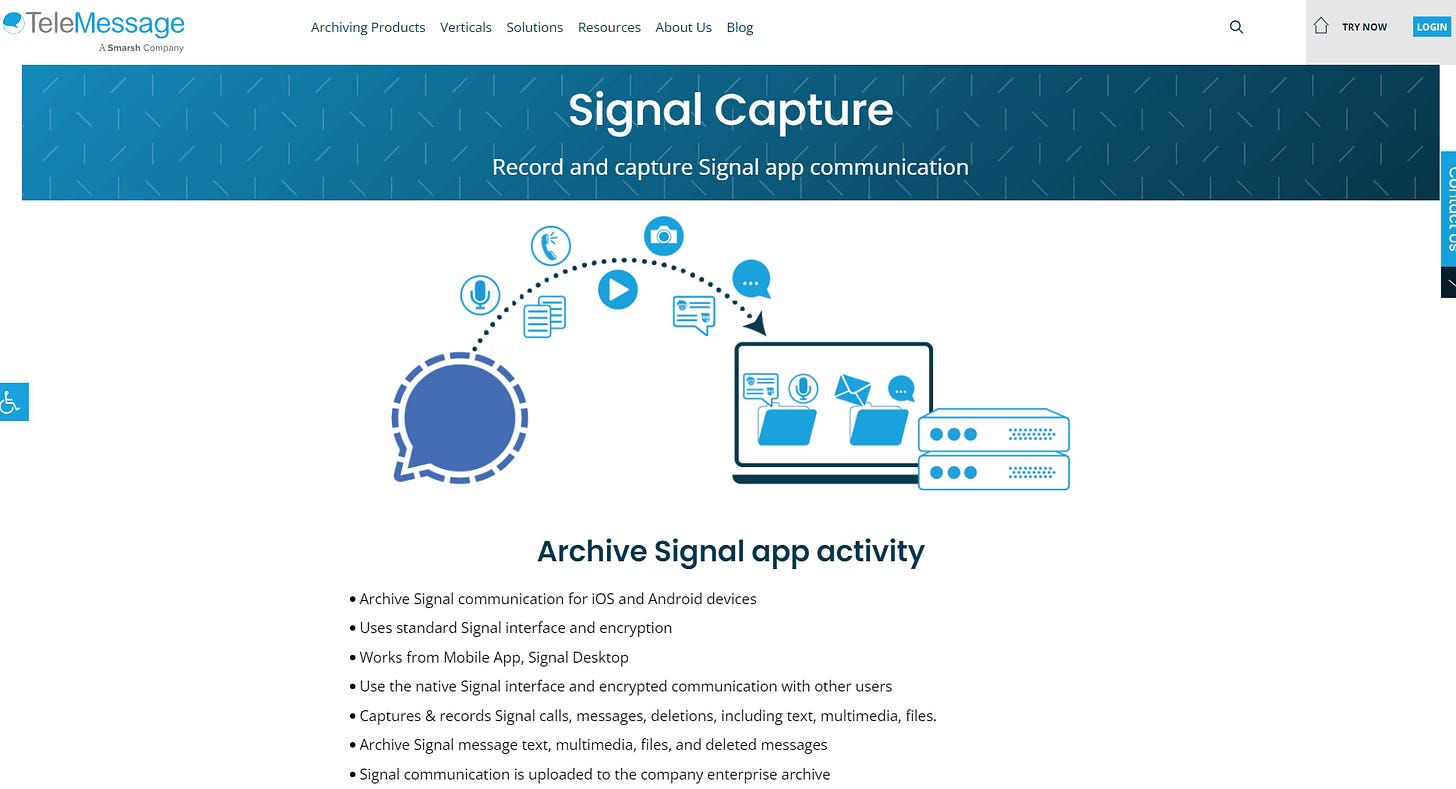
In one of the Reuters photos of Waltz’s phone, a pop up appears with the text “Verify your TM SGNL PIN,” just below a message from Vice President JD Vance. TM SGNL is an aspect of TeleMessage’s software called “Signal Capture” that it sells to governments and corporations to enable archiving.

Waltz’s misuse of the Signal app became one of the Trump Administration’s biggest scandals, when it was revealed that he accidentally added the editor of The Atlantic, Jeffrey Goldberg, to a group chat with top officials. Secretary of Defense Pete Hegseth had laid out details of a forthcoming bombing mission targeting Yemen in the text thread. Aside from cybersecurity and espionage concerns, the incident raised the issue of federal record-keeping laws, after screenshots revealed that the conversations were set to auto-erase. The White House indicated that there were efforts to remedy the situation.
“There have been steps made to ensure that something like that can obviously never happen again, and we’re moving forward,” press secretary Karoline Leavit told reporters amid the scandal. When asked whether the White House contracted TeleMessage’s archive app to attempt to rectify record-keeping concerns, the White House did not respond to a request for comment.
“These are the public’s records and the details for how agencies save records is really important. Just ‘archiving’ them using a shady software vendor is not a real plan,” said Freddy Martinez, co-director at Lucy Parsons Labs, a researcher who studies surveillance and an expert in government record-keeping regulations. Despite the app’s appearance as a clone of Signal, the app’s exfiltration of data to other machines introduces risk, Martinez explained. “App developers like Signal are extremely protective because they know the risks when someone else claims they have ‘secure’ implementations of their code.”
It’s unclear how the White House would implement a TeleMessage archive system. The company offers governments and businesses the option to exfiltrate data that automatically sends copies of messages to servers on-site or in the cloud. Compared against the traditional Signal app, this additional element introduces a greater risk whereby the secondary archival device could be accessed and rendered insecure.
The personal smartphones of U.S. national security officials are liable to be prime targets of spyware by foreign adversaries, including U.S. allies. When the revelations of widespread Signal usage were first published, many speculated about the endpoint security of senior Trump official’s smartphones.
Although Signal’s end-to-end encryption technology works, it’s only as secure as the device. If a device is infected with spyware, the messages displayed on the user’s screen would be vulnerable to a foreign government’s hackers. This Signal Capture app, made by TeleMessage, would appear to only increase the vulnerability of the information by automatically copying messages to other servers or devices.
A Signal spokesperson, who did not give a name because of the extreme sensitivity of the matter, told Drop Site, “We cannot guarantee the privacy or security properties of unofficial versions of Signal.”
Israel’s tech world is small, and Israel leads the world in exports of spyware and digital forensics tools. Former Israeli Defense Forces intelligence officials have gone on to found tech companies, especially in the field of spyware and surveillance. Companies like NSO Group, maker of the controversial Pegasus spyware, were founded and staffed by Israeli officials. The company was sanctioned by the Biden Administration. Israeli spyware firms have become known for selling their products to oppressive regimes around the world, where the tech is often used to target human rights advocates, journalists, and dissidents.
TeleMessage was founded in 1999, the same year its founder left his Israeli military intelligence job. The company found early success in the burgeoning world of text message technology. The company grew and eventually pivoted to focusing on extracting messages from common communication platforms for the purposes of archiving, often to meet record keeping regulations.
Tech professionals have moved between companies like TeleMessage and some of the leading Israeli spyware firms. For example, Alon Falah, a technical support manager at TeleMessage until 2021, left the company to join NSO Group, according to his LinkedIn profile. Another employee, Itzhak Demoza, joined Telemessage last year after a stint at Cellebrite, maker of hardware and software widely used by law enforcement to extract data from smartphones.
TeleMessage’s founder and top employees likewise share Israeli military intelligence backgrounds.
Guy Levit, TeleMessage’s CEO, “served as the head of the planning and development of one of the IDF’s Intelligence elite technical units” from 1996 until 1999, according to his official biography.
Gil Shapira, TeleMessage’s Vice President Business Development, served in the “Israeli Air Force from 1993 – 1999 as a computer programmer, project manager and team leader,” according to his bio.
Nir Elperin, the Vice President of Corporate Strategy “served 4 years in the Elite Military Intelligence Unit of the Israeli Defense Forces,” according to his bio, where he “commanded teams of computer experts.”
A mobile researcher at TeleMessage, Aviv Tzitayat worked for Israeli Military Intelligence as recently as February 2021, according to his LinkedIn profile. There, he worked as a “Reverse Engineer and Software Developer.”
Another employee, Maor Ben Abu, previously served with Unit 8200, a group within Israeli military intelligence specializing in clandestine operations, signals intelligence, and counterintelligence. The unit has been compared to the National Security Agency, and its graduates frequently go on to work in the cyber warfare industry.
Israel has a long history of espionage and surveillance in the United States. In 1998, it was identified by the US National Counterintelligence Center to be on the Department of Energy’s Sensitive Country List. In a 2000 report, NCIC listed Israel as one of the “most active collectors of intelligence against the private sector.” Despite the close relationship between the United States and Israel, the Associated Press reported that the CIA’s Near East Division considered Israel the Number 1 counterintelligence threat in 2012. In 2019, the U.S. government determined that Israel had most likely planted “StingRay” surveillance devices that mimic cell phone towers around the White House, intending to spy on President Donald Trump and his top aides, according to a Politico report. Israel denied the allegations.
A review of federal contracting data shows TeleMessage has a history of contracting with the Department of State and Health and Human Services. The company acknowledges its work with the federal government on its website. When reached for comment, a representative would not confirm or deny the White House had purchased licenses for their apps, but acknowledged they sell technology to US local and federal government agencies.
Have tips about the US government’s usage of communication apps like TeleMessage? Contact Jason securely on Signal at jpal.01






