Mishaal Rahman / Android Authority
TL;DR
- Google’s updated Play Integrity API is making it significantly harder for users with rooted phones or custom ROMs to access certain applications due to enhanced security verifications.
- The update, now rolling out by default as of May 2025, enforces stricter hardware-backed security signals for integrity verdicts on devices running Android 13 or later.
- While this change aims to protect apps from abuse, it negatively impacts legitimate power users and potentially those on older devices lacking recent security patches.
Compared to the billions of regular Android users, the number of people who root their Android phones or install custom ROMs is minuscule. While I wouldn’t say Google is actively hostile towards these power users, the company’s efforts to strengthen Android app security have the unfortunate side effect of negatively impacting their experience. Google’s latest update to the Play Integrity API, for example, makes it easier for developers to protect their apps from abusive users while also making it significantly harder for legitimate power users to utilize certain applications.
The Play Integrity API is a tool developers can use to verify that inbound interactions and server requests come from an unmodified version of their app binary running on a genuine Android device. Many developers use this API to mitigate app abuse that could lead to revenue or data loss. For example, the API can help prevent users from accessing premium content without paying, or it can help safeguard sensitive financial data by preventing access on devices that could potentially be compromised.
The problem for power users who root their phones or install a custom ROM lies in Google’s definition of a “genuine” Android device: one running a Google Play-certified build of Android. This definition inherently excludes nearly every custom ROM, prompting many custom ROM users to employ hacks to spoof certified builds. While many people who root their phones don’t install a custom ROM, they do unlock the bootloader as part of the rooting process. This step causes their devices to fail the more stringent Play Integrity checks, locking them out of many dining, medical, gaming, banking, and payment apps, as these types of apps often utilize the API’s stricter evaluations.
Previously, the Play Integrity API and its predecessor, the SafetyNet Attestation API, weren’t as much of a concern for power users, as they could often find easy workarounds. However, Google has been moving to enforce hardware-backed security signals. These are significantly harder to bypass because, unlike simpler past methods, they are rooted in the hardware itself. While these hardware-based checks offer more robust security, power users had found some reprieve in the fact that Google wasn’t universally enforcing their strictest application.
Furthermore, it was up to app developers to decide whether they wanted hardware-backed security signals to be enforced. This gave developers the flexibility to restrict their apps’ usage as they saw fit. For example, banking or payment apps often went out of their way to check that devices passed hardware-backed signals, but now, these signals are part of Play Integrity’s baseline for all integrators of the API.
In December of last year, Google announced a major update to the Play Integrity API that enhances the “basic,” “device,” and “strong” integrity verdicts on devices running Android 13 or later. The “device” and “strong” integrity verdicts are the two more stringent verdicts apps can receive when calling the Play Integrity API. The “basic” verdict, while less stringent, is also not as widely used by developers seeking higher levels of security.
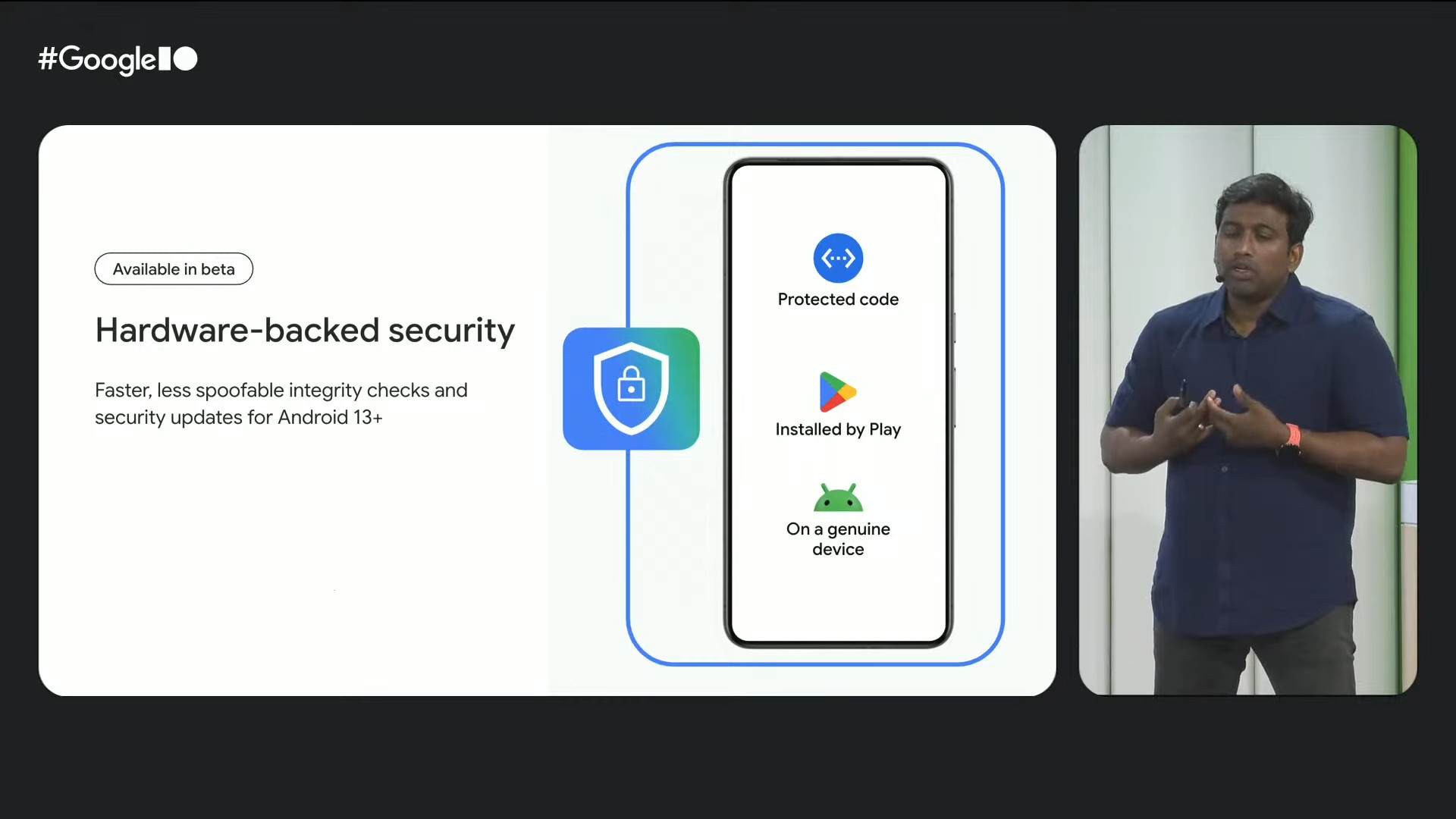
In the past, only the “strong” integrity verdict used hardware-backed security signals. Starting in December of last year, however, Google made all integrity verdicts even stricter: the “device” integrity verdict was updated to also use hardware-backed security signals, while the “strong” integrity verdict was revised to require a security patch level from within the last year. Meanwhile, the “basic” integrity verdict was also updated to use hardware-backed signals, though due to its less stringent requirements, it passes even on devices with root enabled or the bootloader unlocked.
Google’s stated reasoning for this change was to make the Play Integrity API faster, more reliable, and more private for users by reducing the number of signals that need to be collected. These changes also make the API harder and more costly for attackers to bypass.
At the time of the announcement, these updated integrity verdicts weren’t immediately enforced. Google made them opt-in for developers but stated that all “[Play Integrity] API integrations would automatically transition to the new verdicts in May 2025.”
Well, it’s now May, and Google is making good on its promise. At Google I/O 2025, the company announced that it had flipped the switch and made all integrity verdicts stronger by default. During the “what’s new in Google Play” session, Raghavendra Hareesh, the Lead of Play Developer and Play Monetization at Google, said that the company is “rolling out stronger verdicts for all developers with no additional developer work required.”
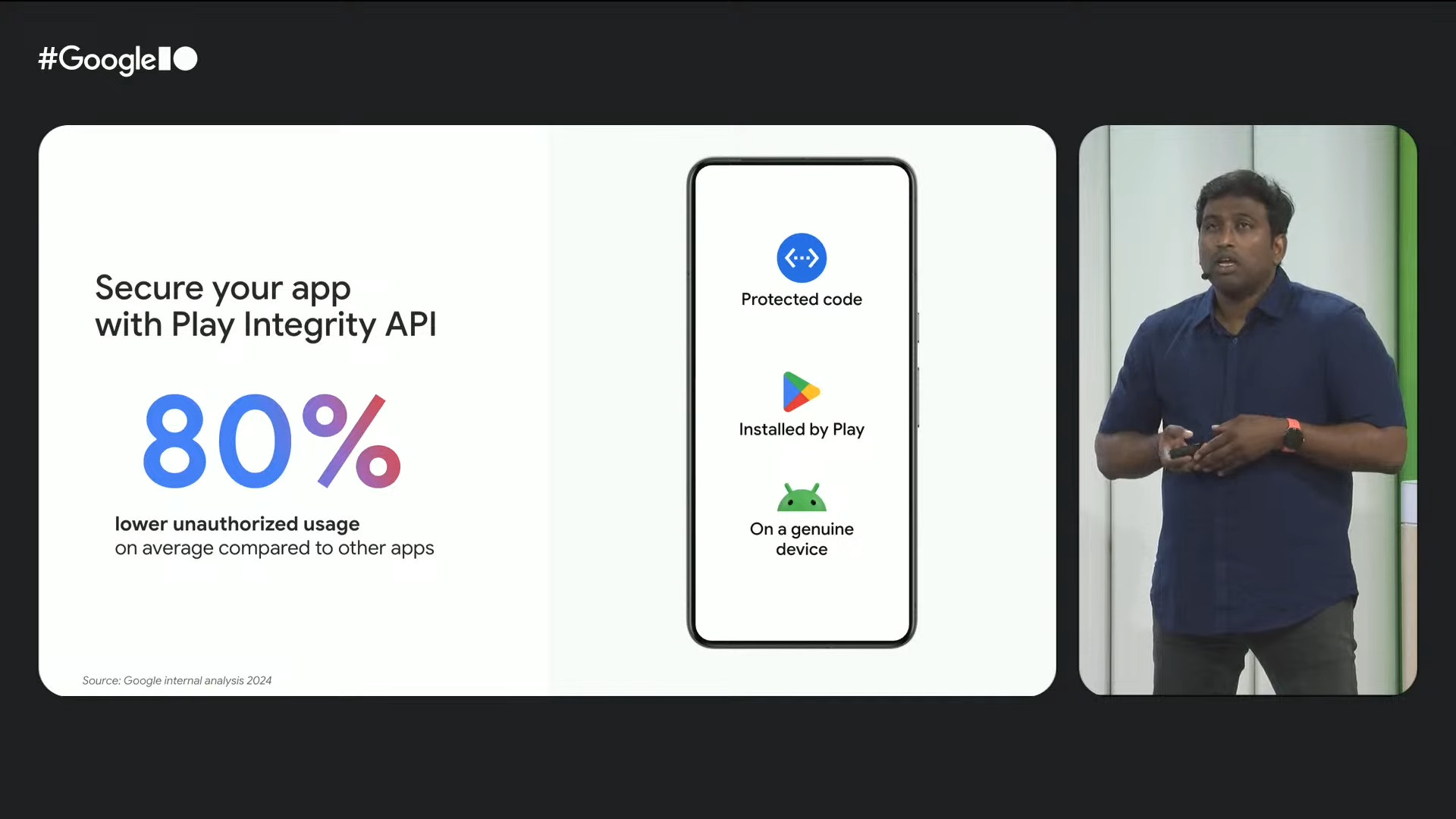
“The Play Integrity API is a vital tool in any comprehensive security strategy. Helping you defend your entire app experience. It’s crucial in preventing abuse that can lead to revenue loss and also harm your users. Developers who have been using this API are seeing over 80% lower unauthorized usage compared to other apps. That means less fraud, less cheating, or data theft.
And we are continuing to evolve this Play Integrity API to stay ahead of all the threats that are out there. So today we are rolling out stronger verdicts for all developers with no additional developer work required. This makes it faster, more reliable, and more privacy-friendly to check if a device is trustworthy. Developers can also now check if a device has recently installed a security update, which is very important for apps which are protecting sensitive actions.” Raghavendra Hareesh, Lead of Play Developer and Play Monetization at Google
This means that power users who root their phones or install a custom ROM may suddenly find some apps stop working, especially on devices running Android 13 or later. Even users with unmodified Android 13+ devices might face problems if their devices haven’t received a software update in a while. This is because apps checking the “strong” integrity verdict require a recent security patch level to pass.
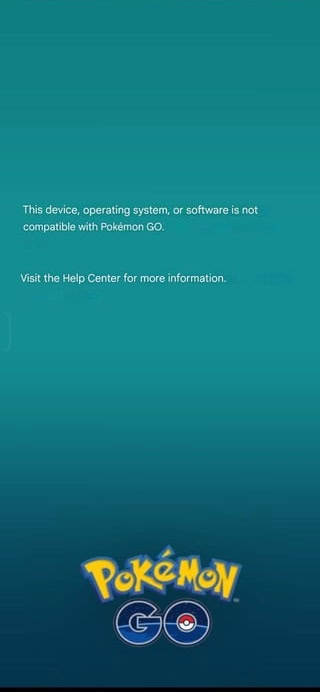
Mishaal Rahman / Android Authority
Error message in the Pokémon Go app when the device fails its Play Integrity checks
Google’s full implementation of hardware-backed security signals has been anticipated for some time. While power users previously found simple ways to bypass earlier measures — often by tricking the Play Integrity API into relying on more easily spoofed software-based checks — these methods were never permanent solutions. It was, therefore, only a matter of time before these users would encounter broken apps.
Soon, easy workarounds will likely vanish, leaving users with no choice but to either resort to shady keybox leaks or to restore their devices to stock. So, while Google’s primary aim with these changes is to improve app security for everyone, they nonetheless degrade the experience for these power users.
Thanks to security researcher linuxct for his inputs on this article!